An increasingly popular database choice amongst security teams is AWS DynamoDB. The key-value storage, simplicity, scalability, and security offered by DynamoDB make it suitable for the kinds of data storage tasks common in security operations and incident response, especially if they already use AWS.
In this post, we’ll explore how security teams can use DynamoDB in their automation Stories.
Authenticating to AWS DynamoDB from Tines
To begin integrating Tines with AWS DynamoDB, we first need to create a credential. In your AWS console, create an IAM user with the appropriate permissions to perform actions in DynamoDB. Take the access key and access secret for the user and enter them into a new Tines AWS mode credential.
Next, specify a name for the credential and choose the AWS region you will be working with. Finally, under service name enter ‘dynamodb’.
When finished your Tines AWS credential should look like the below:
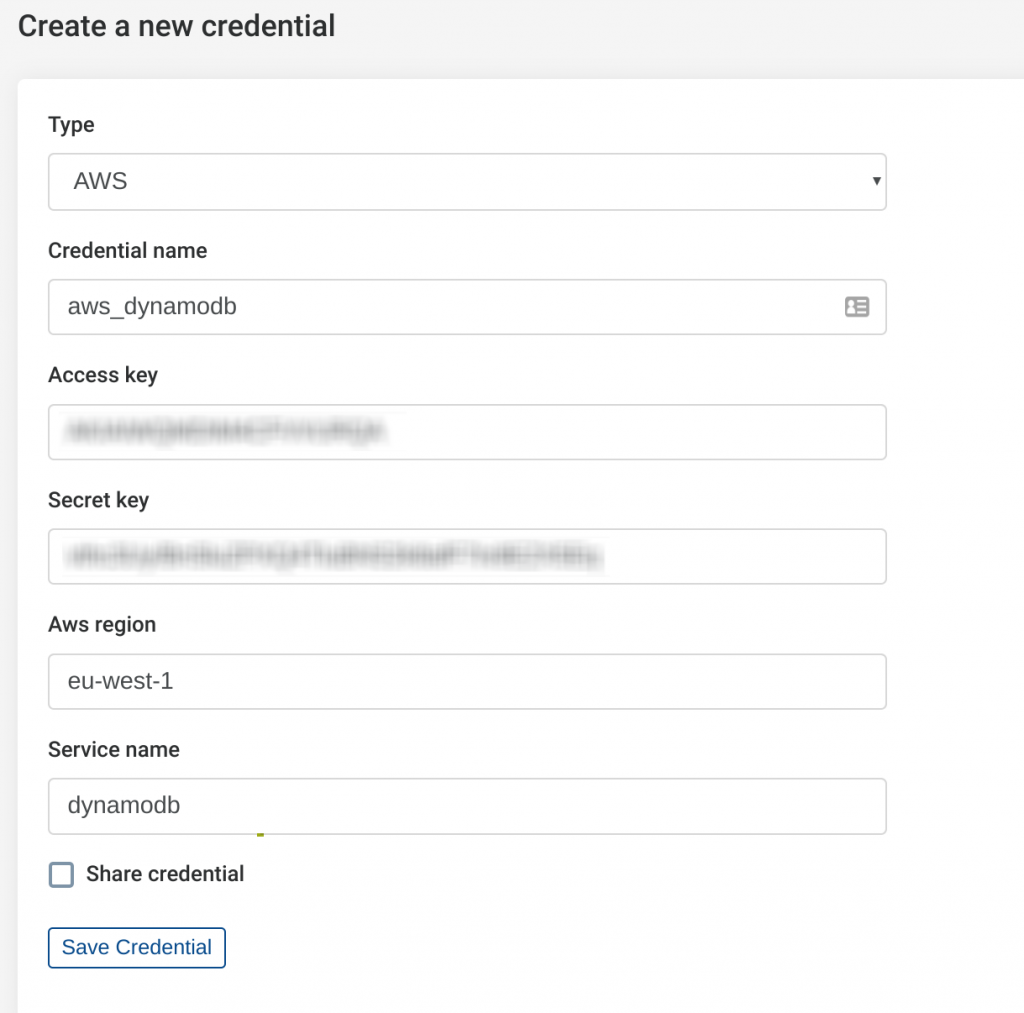
Creating a Tines AWS credential
Using the AWS Credential
AWS credentials work a little differently from the other credential modes in Tines. When an HTTP Request Action with an AWS mode credential included in a header called “Authorization” runs, Tines will use the AWS Signature Version 4 Signing Process and include the corresponding auth headers in the request before submitting it to AWS.
For example, the below HTTP Request Action uses an AWS mode credential (aws_cloudtrail) to list cloudtrails in the us-east-1 region.
{
"url": "https://cloudtrail.us-east-1.amazonaws.com",
"method": "get",
"content_type": "form",
"payload": {
"Action": "DescribeTrails",
"Version": "2013-11-01"
},
"headers": {
"Authorization": "{% credential aws_cloudtrail %}"
},
"expected_update_period_in_days": 1
}When this Action runs, the request will be signed and will be converted to the following before being sent to AWS:
"url": "https://cloudtrail.us-east-1.amazonaws.com",
"method": "get",
"content_type": "form",
"payload": {
"Action": "DescribeTrails",
"Version": "2013-11-01"
},
"headers": {
"X-Amz-Date": "20190403T212241Z",
"Authorization": "AWS4-HMAC-SHA256, Credential=AKIAJQPQOWURT6TXRN5Q/20190403/us-east-1/cloudtrail/aws4_request, SignedHeaders=content-type;host;x-amz-content-sha256;x-amz-date, Signature=57d317eaa8e9f17883a828385782dc069fd04391c0e335642785bfd99452cc44",
"X-Amz-Content-Sha256": "e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855"
DynamoDB Tines Agents
Tines can perform all available DynamoDB Actions. The following Action examples cover a selection of the most common.
List Amazon AWS DynamoDB Tables
{
"url": "https://dynamodb.eu-west-1.amazonaws.com",
"method": "post",
"content_type": "json",
"payload": {},
"headers": {
"Authorization": "{% credential Aws_DynamoDB %}",
"X-Amz-Target": "DynamoDB_20120810.ListTables"
}
}
Scan an Amazon AWS DynamoDB table with a filter
{
"url": "https://dynamodb.eu-west-1.amazonaws.com",
"method": "post",
"content_type": "application/json",
"payload": {
"TableName": "tines_test",
"FilterExpression": "age > :val",
"ExpressionAttributeValues": {
":val": {
"N": "10"
}
}
},
"headers": {
"Authorization": "{% credential aws_dynamodb %}",
"X-Amz-Target": "DynamoDB_20120810.Scan"
}
}
Scan an Amazon AWS DynamoDB Table
{
"url": "https://dynamodb.eu-west-1.amazonaws.com",
"method": "post",
"content_type": "json",
"payload": {
"TableName": "TestTable",
"AttributesToGet": [
"Id"
]
},
"headers": {
"Authorization": "{% credential Aws_DynamoDB %}",
"X-Amz-Target": "DynamoDB_20120810.Scan"
},
"expected_update_period_in_days": 1
}Delete an Amazon AWS DynamoDB table
{
"url": "https://dynamodb.eu-west-1.amazonaws.com",
"method": "post",
"content_type": "json",
"payload": {
"TableName": "tines_test"
},
"headers": {
"Authorization": "{% credential aws_dynamodb %}",
"X-Amz-Target": "DynamoDB_20120810.DeleteTable"
}
}Create an Amazon AWS DynamoDB Table
{
"url": "https://dynamodb.eu-west-1.amazonaws.com",
"method": "post",
"content_type": "json",
"payload": {
"KeySchema": [
{
"KeyType": "HASH",
"AttributeName": "Id"
}
],
"TableName": "TestTable",
"AttributeDefinitions": [
{
"AttributeName": "Id",
"AttributeType": "S"
}
],
"ProvisionedThroughput": {
"WriteCapacityUnits": 5,
"ReadCapacityUnits": 5
}
},
"headers": {
"Authorization": "{% credential Aws_DynamoDB %}",
"X-Amz-Target": "DynamoDB_20120810.CreateTable"
}
}Add an item to Amazon AWS DynamoDB table
{
"url": "https://dynamodb.eu-west-1.amazonaws.com",
"method": "post",
"content_type": "json",
"payload": {
"Item": {
"job": {
"S": "engineer"
},
"name": {
"S": "fred"
},
"age": {
"N": "20"
}
},
"TableName": "tines_test"
},
"headers": {
"Authorization": "{% credential aws_dynamodb %}",
"X-Amz-Target": "DynamoDB_20120810.PutItem"
}Get an item from an Amazon AWS DynamoDB table
{
"url": "https://dynamodb.eu-west-1.amazonaws.com",
"method": "post",
"content_type": "json",
"payload": {
"Key": {
"name": {
"S": "alice"
}
},
"TableName": "tines_test"
},
"headers": {
"Authorization": "{% credential aws_dynamodb %}",
"X-Amz-Target": "DynamoDB_20120810.GetItem"
}
}
Delete an item from an Amazon AWS DynamoDB table
{
"url": "https://dynamodb.eu-west-1.amazonaws.com",
"method": "post",
"content_type": "json",
"payload": {
"Key": {
"name": {
"S": "fred"
}
},
"TableName": "tines_test"
},
"headers": {
"Authorization": "{% credential aws_dynamodb %}",
"X-Amz-Target": "DynamoDB_20120810.DeleteItem"
}
}Summary
By including DynamoDB Actions in Tines automation Stories, security teams can quickly and reliably fetch and store important data, allowing them to enrich security incidents and make better decisions around incident investigation and remediation.
*Please note we recently updated our terminology. Our "agents" are now known as "Actions," but some visuals might not reflect this.*